This article describes the key aspects of firewall configuration and proper placement of the application and DBMS that ensure maximum operation and security of the ELMA365 system.
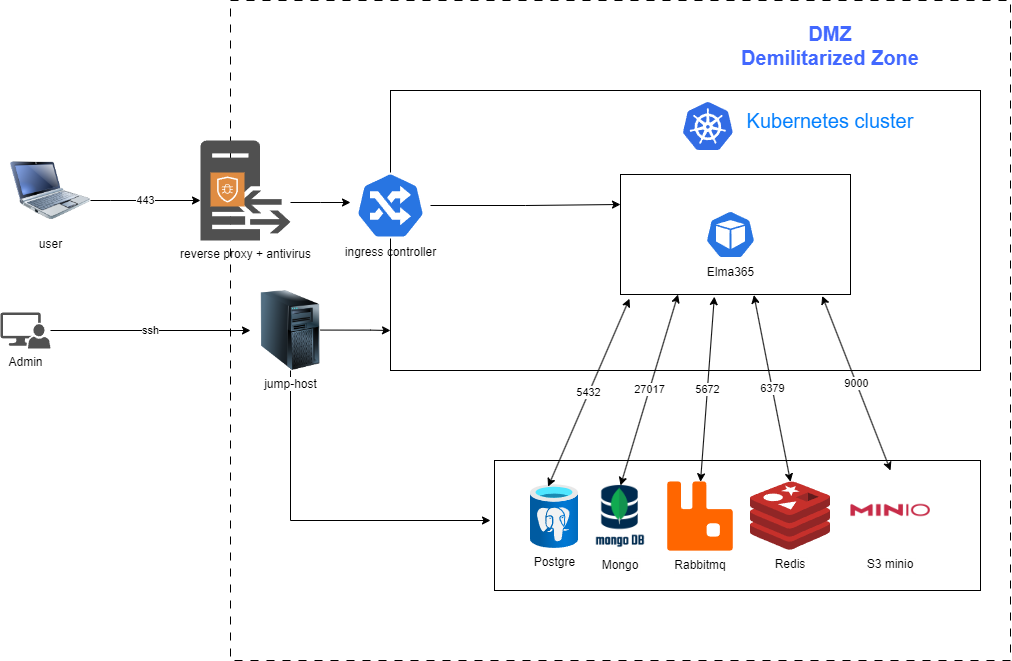
ELMA365 is a microservice solution that utilizes Golang, NodeJS, Angular, PostgreSQL, MongoDB, RabbitMQ, Redis, Docker, Kubernetes, and S3 MinIO protocol for file storage. The location of the application and DBMS in the DMZ (Demilitarized Zone) and traffic control by means of a firewall will ensure the security of the ELMA365 system operation.
Antiviruses may slow down the ELMA365 application because they scan traffic between containers and the database, as well as scan files and cache information in memory. Checking the DBMS readable files does not suggest the presence of malicious code, so this procedure is not useful and slows down the application.
ELMA365 application and DBMS communicate through certain ports. Checking the traffic through these ports may also slow down the work, as the application actively interacts with the DBMS. The antivirus checks each message sent between the application and DBMS without forwarding it directly.
It is recommended to install the antivirus on the reverse proxy on the DMZ boundary. This will avoid automatic traffic checking between the application and DBMS, as well as maximize the speed and security of the system operation.
If you need to install an antivirus despite the above recommendations, you should add the following internal ports to the exclusions for KinD and Microk8s versions of ports 443 and 80 for user interaction:
- To interact with the database: 5432, 27017, 6379, 5672, 9000;
- To interact with services: 33349, 10248, 25000, 10249, 9099, 10251, 10252, 10256, 19001, 1338, 6010, 33955, 10250, 10255, 10257, 10259, 16443.
The directories /opt/elma365/ and /var/lib/docker/overlay2/, as well as the following databases and processes, should also be included in the exceptions:
ELMA365 application databases:
- /opt/bitnami/postgresql/bin/postgres;
- /opt/bitnami/mongodb/bin/mongod;
- /opt/bitnami/mongodb/bin/mongo;
- redis-server;
- /opt/bitnami/redis/bin/redis-server;
- /opt/bitnami/erlang/lib/erlang/erts-12.3.1/bin/beam.smp;
- /opt/bitnami/rabbitmq/sbin/rabbitmq-server;
- minio;
- /opt/bitnami/minio/bin/minio server.
ELMA365 application processes:
- /bin/sh;
- /coredns;
- /hostpath-provisioner;
- /nginx-ingress-controller;
- /opt/bitnami/erlang/lib/erlang/erts-12.3.1/bin/epmd;
- /sbin/dinit;
- /snap/microk8s/3410/bin/containerd;
- /snap/microk8s/3410/bin/containerd-shim-runc-v1;
- /snap/microk8s/3410/kubelite;
- /srv/elma365ctl-server;
- /usr/bin/dumb-init;
- /usr/bin/kube-controllers;
- /usr/libexec/git-core/git-daemon;
- /usr/local/bin/node;
- /usr/local/bin/runsvdir;
- calico-node;
- git daemon;
- gpg-agent;
- nginx: cache manager process;
- nginx: master process;
- nginx: worker process;
- runsv;
- sh;
- ELMA365 internal processes.
Contact ELMA365 tech support for a list of internal processes.
Found a typo? Highlight the text, press ctrl + enter and notify us